With waves of ransomware and hacks hitting users more and more each passing day, I thought I’d share a few simple steps you can take to help protect your files and avoid falling victim to these extortion scams, including Windows’s built-in ransomware protection function.
What is ransomware?
Ransomware is really just a virus or other malicious software, but with an added twist: instead of destroying your files outright, ransomware scrambles them in order to block access to either those files (or your entire computer system) until a sum of money is paid — quite literally holding your computer for ransom. Most other hallmarks of malware are still utilized as well: for example, ransomware will often try to spread to other computers, email itself to everyone in your address book (which will appear to the recipients as if you sent them the message in an attempt to trick them into opening it) and more.
Also keep in mind that even paying the ransom may not revive your files: how can you actually trust the criminals will (or even have the ability to) unlock your files once you’ve paid them? You can’t.
Never open links, emails, or files that you don’t fully trust — even if they appear to have come from a close relative, friend, or coworker. When it doubt, throw it out.
First: Trust no one
You are the first line of defense in your security, so the #1 most important thing you can do is to avoid clicking links or opening emails/attachments that you aren’t expecting (even if they appear to come from a close relative, friend or coworker). Your vigilance here will protect you more than any technological solution can.
When you open a program, it essentially is enjoying the same access that you have to your system, and you are implicitly trusting the program won’t abuse that access. This is not unlike handing a physical photo album to a houseguest and trusting they won’t start ripping out pages or lighting it on fire. While 99.999% of the people in your life would never dream of destroying your memories in such a grievous manner, you are still implicitly trusting them to handle your photos with care when you hand them the folder.
Your files on your computer are no different. For example, you trust that your picture gallery program isn’t going to corrupt and destroy every photo in your collection. Every time you open a file, click a link, or run an app, you are trusting it to be just as courteous as that houseguest, and this trust can be exploited. Avoid this pitfall by heavily scrutinizing every link, file, or app you click. When in doubt, throw it out.
Next, consider that when you run a program, that program can do anything you can do. Even if you would never dream of deleting all your important files, you technically could do so: nothing prevents you from selecting all your files and tapping the “delete” key (and then emptying the trash). And if you can do that, any file you open can also do that. Every file you open has the same access that you have. That’s quite literally how computers function. It bears repeating: every time you open a file, link, or email: you are trusting it not to destroy your data or abuse that trust.
Every file you open has the same access that you have.
Can you trust that every program you install, or every file attachment ever emailed to you, is not going to abuse this power in order to hold your files for ransom? This is too important for a rhetorical: no, you absolutely cannot.
So beyond pure diligence and paranoia, what are some easy technical steps you can take to protect yourself?
Next: Backup, backup, backup.

Even if you manage to avoid viruses and ransomware — a veritable miracle in its own right in modern times — data that isn’t backed up is still as good as gone. Yes malicious software can infect you, but disasters also happen: fires burn, tornadoes destroy, lightning strikes, burglars burgle, floods flood, and hard drives fail. The average lifespan of a typical hard drive is about 3-5 years. Some last longer, some give out sooner, but one thing is for sure, all hard drives will eventually fail. The only way to keep your data safe is to back it up before any of the above occurs – and make sure that backup is stored somewhere else. That way even if your house burns down, the backup will be safe from harm. All too often, homes or businesses are broken into by thieves and the backup drive is stolen right along with the original PC it came from.
Even if my laptop was to sink to the bottom of a lake, I wouldn’t lose a single file.
The method you choose for backing up is entirely up to you. You could meticulously save your important files to discs every night and mail them off to be stored in a safety deposit box, but a better hands-free approach is to use an automatic backup system that runs for you. There’s a ton of tools on the market for this (Norton Online Backup and Carbonite come to mind), but I personally simply store all my files in Microsoft’s OneDrive online file storage service. Other providers have very similar tools: Google Drive, Drop Box, Apple iCloud, Amazon Cloud Drive, and many more. In all cases, your files are stored in two places at once: your own local hard drive, plus an extra copy on the provider’s web server. The file online is kept in perfect sync with your local copy. Every time you edit your files, the online version is updated to match. OneDrive also has the ability to store multiple copies of every file. This allows you to “go back in time” to see older versions of the file such as before a change was made, or before malware destroyed the file.
In this way, even if my laptop was to accidentally sink to the bottom of a lake or all my files got locked by a ransomware attack, I wouldn’t lose a single file: every file I care about keeping is stored in OneDrive, ready to be used from any other computer (or phone or tablet).
Third: Control which apps can access your files
For Windows users, I recommending turning on your Windows PC’s built-in ransomware protection options like Controlled Folder Access. This feature protects your important files from being modified by “unfriendly” applications.
For example, say you downloaded a new weather app from an disreputable website, and it tried to start churning through your documents folder to destroy your files: this feature would block that action from occurring because the app was not allowed to make changes to your protected Documents folder, even though it was running under your user account, this application-based protection restricts what actions a program can take on your behalf.
In 2017, I wrote an article saying that this feature was not ready for primetime because it slightly inconvenienced me. Four years of refinement later, I can say that this function is enabled on every computer I use and has not been an inconvenience in the least in several years. I now enable it on every computer I build, and highly recommend everyone else turns this on as well. Sure you might need to allow an app at some point, but that moment to give permission is an infinitesimal price to pay versus allowing every file you open to have unrestricted access to your data.

Some situations where you may need to provide access would be: allowing a game to modify mod files (gamers will understand what this means), or allowing your photo editing program to save changes to your picture files.
Finally: Increase User Account Control settings
Here’s an option many techy enthusiast types will usually balk at: getting more security warnings. However if you install new software or visit unfamiliar websites this can be a great option to increase. By default, Windows will silently permit certain changes to be made to your system’s configuration, without asking for approval. Many times this means that us power users are running administrative-level (aka “root”) privileged processes without even knowing it.
Turning this option up means you will always be notified anytime an app tries to make changes to your computer (and critically, give you a chance to intervene and deny the changes before they occur).
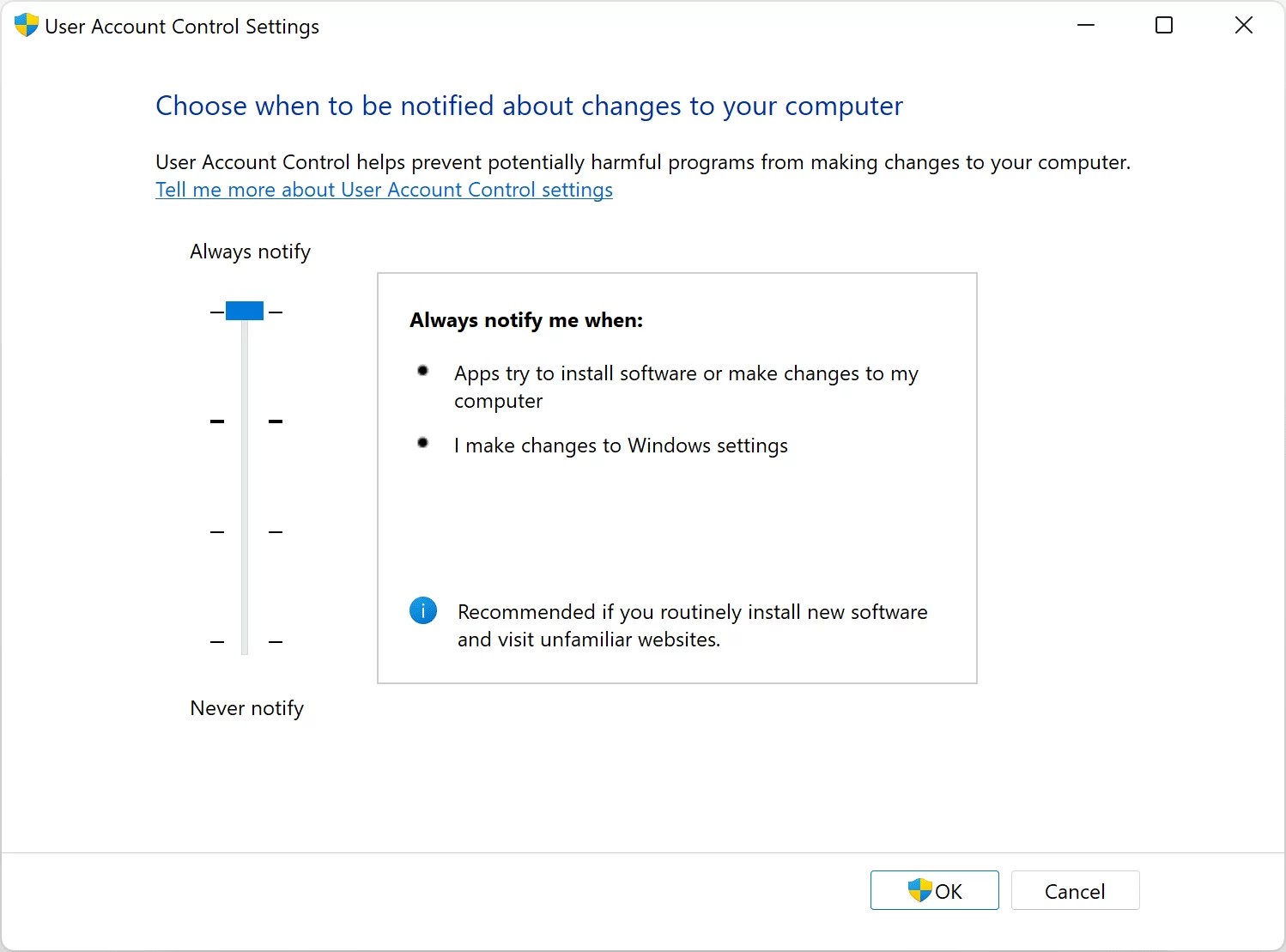
While this may mean that you see some additional prompts, keep in mind these will only be shown when the change being attempted is a system-impacting change that compromises your security. You will know that anytime you see a prompt, you should be scrutinizing it carefully, because it means the action being attempted is requiring you to grant total system authority to the program that’s requesting it (and if you approve, the change the program is making may not be possible to undo).
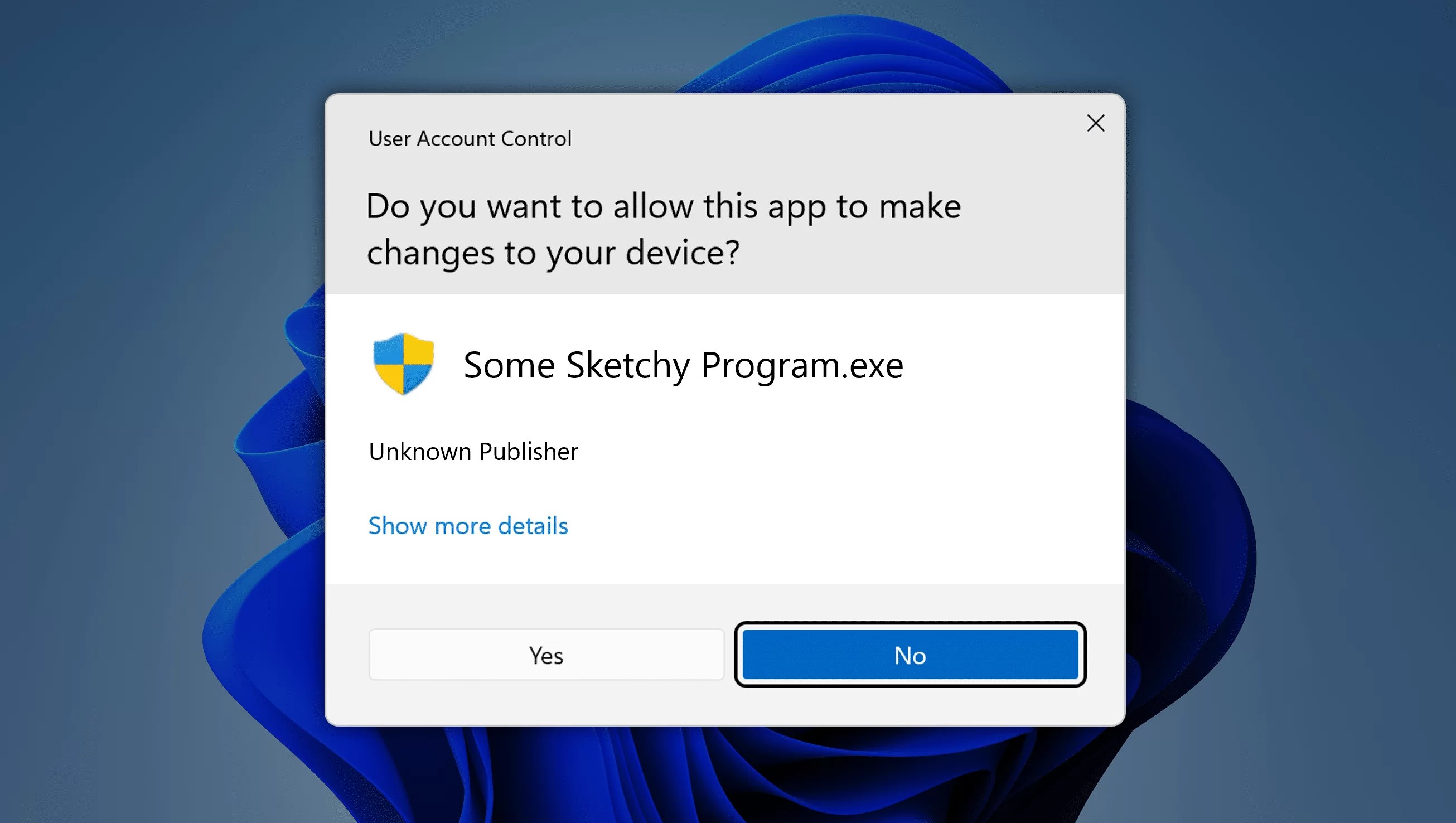
Even when it is yourself that is making the change, this short approval opportunity also provides time (even if just a second) to contemplate the change and consider if you want to continue. For example, downloading and running a simple program from a website might seem benign (and note that simply running a stand-alone EXE you downloaded from the web won’t prompt you for permission). But if it does prompt for permission, you might want to reconsider whether you truly, really want to hand over total administrative access to your computer to that maybe-sketchy program.
For even more security, some security-minded users might decide to make these prompts require typing out your password to give permission (the way Mac or Linux typically do) rather than an all-too-easy to click “yes” button.
Last note on these prompts: just because a program does not prompt doesn’t mean it’s safe – it just means it’s not taking complete root control of your system. Keep in mind that a program doesn’t necessarily need to take total administrative control over your PC to do harm. For example, program only triggers a UAC prompt when it tries to take total administrative access to the computer, but such total control isn’t required to encrypt all the files in your Documents folder. This type of malware might be able to destroy your files, but it can’t destroy all files system-wide unless it prompts for and receives that type of control.
Summary
The tips and suggestions posted here are in no way an exhaustive guide to security, but these are some very simple steps you can take to help avoid falling victim to ransomware or malware, especially for typical low-tech users. These easy steps like careful consideration of opening files and links, having a backup strategy, only installing trusted apps from trusted places, and using your system’s built-in security and protection options can go a long way in keeping you secure.

Leave a Reply